Traditional approaches to cybersecurity are no longer as adequate as they used to be. The old assumption that everything inside the network can be trusted isn’t realistic. Hackers have demonstrated time and time again that no system is impenetrable. We need a new paradigm that accepts this reality.
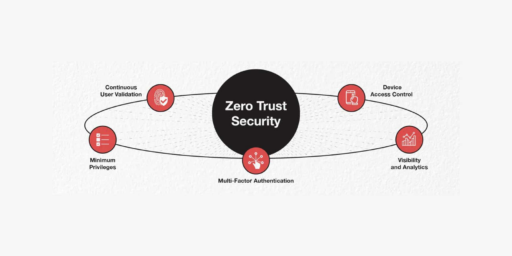
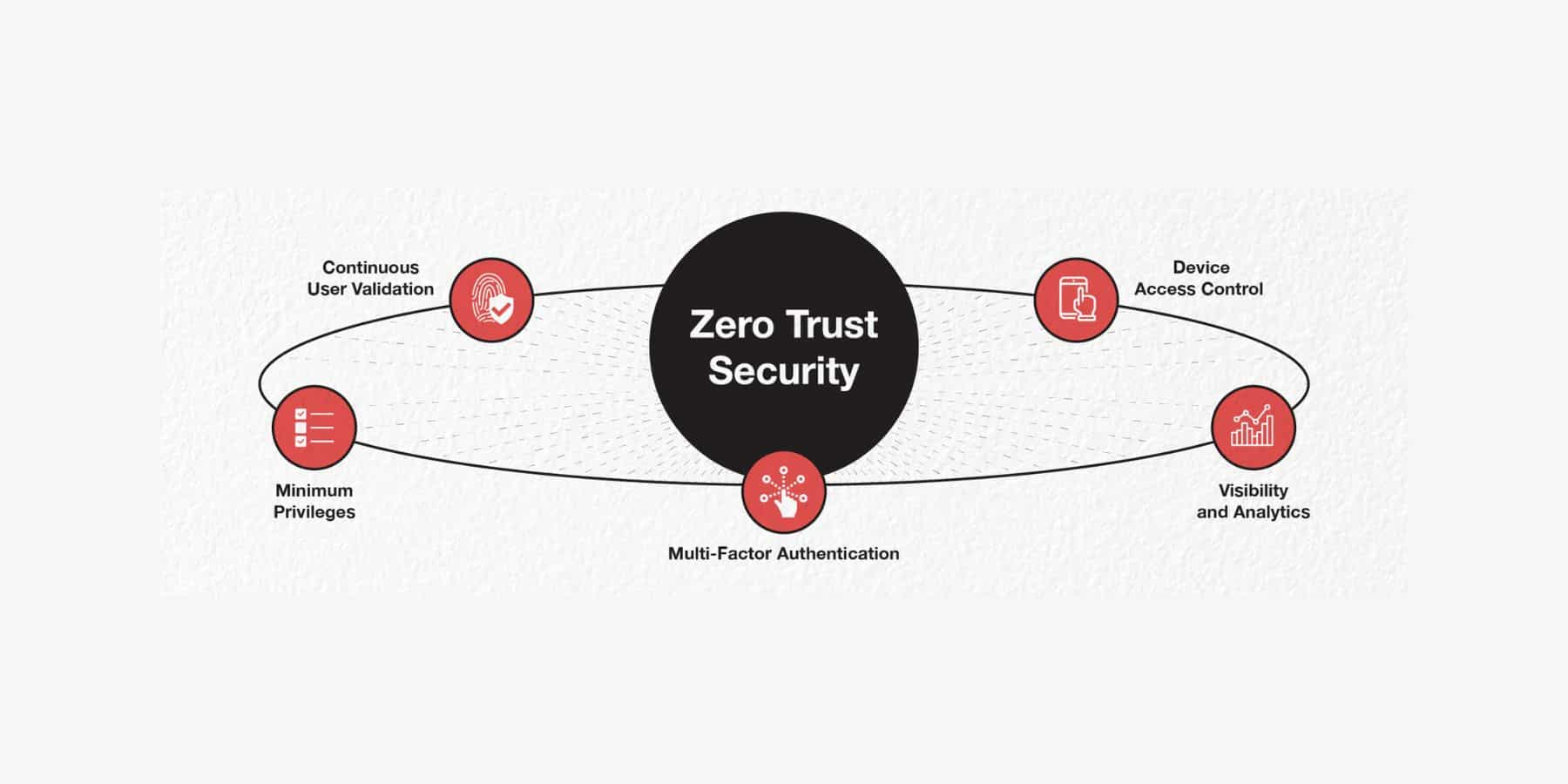
Zero Trust is an emerging framework with a more pragmatic view of security. Instead of placing blind trust in internal users and systems, it takes a “trust nothing, verify everything” stance. Authentication, authorization, and ongoing validation are required for all access, whether from the inside or outside the network. Privileges are strictly limited to what each person truly needs. Breaches are assumed to already exist, so defenses aim to contain damage.
At its core, Zero Trust demands we verify identities, assess risk in real-time, and limit what individuals can access based on their role. Strong passwords and two-factor authentication aren’t enough – we must continuously monitor for anomalies too. Network segmentation prevents lateral movement if intruders do slip in. Encryption and data loss prevention give our information extra layers of protection no matter where it travels.
Transitioning to this model isn’t easy. It requires analyzing our existing practices to shore up weaknesses. Robust identity management, along with micro-segmentation, continuous monitoring, and endpoint security is key. Automation streamlines our processes while analytics help detect subtler threats. Most importantly, everyone must buy into prioritizing security proactively instead of reactively.
Zero Trust isn’t a one-size-fits-all silver bullet. But thoughtfully incorporating its principles can meaningfully elevate our posture over other options. While the work is significant, the potential rewards of improved resilience are well worth the effort. Our information assets and users deserve no less. It’s time we embraced a philosophy of verification over unwarranted faith.